Aleksander Ludynia, Chief Security Officer at Shiji Group, create an easy-to-follow Hotel Cybersecurity Checklist for hoteliers like you. In the current era of digitization, safeguarding the data and systems of hotels from cyber threats has become increasingly vital. Enhance your Hotel's Cybersecurity with our New Free Checklist!
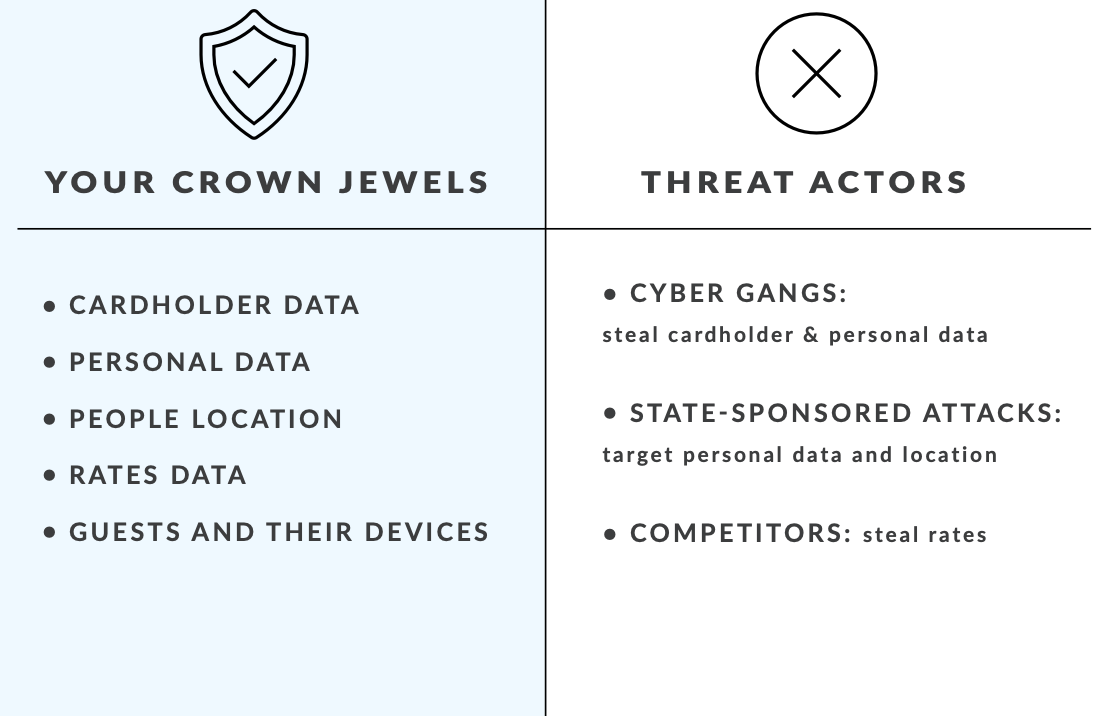
The large amount of customer data processed by hotels is its crown jewel. Whether it is data that can be used to steal money, such as payment or credit card data, or personal and location data that can be used for other nefarious ends, hotels deal with these two types of critical customer information valuable to cyber criminals on a daily basis. On top of it, they also handle sensitive information on rates, which can be of interest to competitors in the same industry.
Hotels need to staff these roles even though the technology isn’t their core business. These will be the people guiding the efforts of the rest of the personnel, as security is everyone’s job.
Conduct audits of all data handled by your hotel that can be considered sensitive in order to understand your risk profile, including the systems used to process and store data, and then map the data flow to identify all the places where information can be.
Common points are legacy systems, which are hard to protect against new threats and to connect to new solutions in a secure manner; inexperienced or temporary staff who may not follow security protocols thus becoming a bridge by knowingly or unknowingly deploying viruses to the network; bad habits, such as staff writing credit card numbers in pieces of paper when in a rush or keeping passwords in unprotected places; and third-party systems with which hotels exchange information such as payments, reservations, invoicing, door locks, TV access, and many other types of vendors that are necessary for daily operations.
Once this is done, list down the threats and risks that may affect the data, considering the possible threat actors and attack methods your system may be vulnerable to.
When all the data, systems, and possible threats are identified, it is time to protect them – especially your crown jewels. Knowing what needs to be protected ensures that you will be able to choose a security solution to apply, as well as an ideal secure configuration to harden all of your key systems.
Make sure you grant appropriate levels of access to each department or role in the proper way, by managing access privileges and monitoring them. Control who has access to what kind of information and for what reasons, so that each person is only able to see what is necessary for them to fulfill their duties.
Often, cybercriminals do not target specific businesses, they are just opportunistic, and thus make use of bots to find vulnerabilities that can be exploited. Vulnerability management and basic cybersecurity hygiene are key to preventing being the low-hanging fruit for these criminals.
Monitoring access regularly helps in identifying breaches or leaks early, and gives you time to react to them. Keep track of traffic of users, applications, and networks.
Many companies think that simply having an antivirus solution means they are safe, but malware is very dangerous. It’s necessary to pick the best solution, configure it properly, and make sure that it’s deployed everywhere, and that it is indeed effective.
Endpoints (such as mobile devices, browsers, and office computers) are usually the first step in the biggest cyber attacks, as criminals rarely start attacks with something big, like going directly for servers. They’d rather attack one person to get access to that person’s workstation and then use it as an access point to go deeper into the company. Monitoring network traffic at each endpoint is crucial, and if you detect attacks at a very early stage, while still at the endpoint, you may be able to stop most of the attacks.

Your systems may interact with that of third-party vendors or suppliers, so it is necessary to manage that interaction and ensure its security. There have often been incidents in the last years, usually very large-scale ones, where the culprits were hacked vendor systems which then allowed access to other businesses’ data. As for legacy systems, they tend to be more vulnerable as security patches stop being released, making them susceptible to modern forms of attack.
Provide good training to employees on how to spot phishing and other sorts of attacks conducted by cybercriminals to decrease the likelihood of one of them becoming the access point. However, it is important to introduce and periodically improve incident management processes: have procedures in place in the case of an emergency or a disaster caused by a successful attack, meaning keeping constant backups and setting recovery processes in place.
Last but not least, test your security often. Conduct penetration testing to verify your security level and make sure it is up to par. This can be done through auditing, conducting technical tests, or using external or internal penetration testers to verify the actual security of your systems.
Download the full checklist >
 |
The Importance Of Cybersecurity
Cybersecurity is of paramount importance to all businesses, however, in the case of the Hospitality Industry, it is quite a unique situation. Hotels tend to handle and own a very large amount of data, sometimes in the hundreds of millions of records for some of the bigger brands, which makes them a prime target for cybercrime. And this encompasses not only crimes against guest information but also against the business itself, as can happen with rate information that may be stolen and sold to benefit a competitor.
There are different risks involved, but the biggest incidents that have happened in the industry were related to cardholder data and leaks of personal data, and when we are talking about such a huge database, the repercussions in the media and beyond can be devastating to the business. It has become more important than ever to protect this precious reservoir of information, and hotels should pay attention to the risks incorporating technology brings to their operations, even though cybersecurity isn’t inherently their core responsibility.
The Crown Jewels of Hotel Data
The large amount of customer data processed by hotels is its crown jewel. Whether it is data that can be used to steal money, such as payment or credit card data, or personal and location data that can be used for other nefarious ends, hotels deal with these two types of critical customer information valuable to cyber criminals on a daily basis. On top of it, they also handle sensitive information on rates, which can be of interest to competitors in the same industry.
But what we’re now seeing is them taking the next step. Fundamentally, if hotels want to take payments and use them as an enabler, they need to start thinking about what omnichannel and unified commerce bring. Omnichannel is a pretty well-known term denoting the offering of multi-sales channels to guests, and unified commerce is about linking those different channels to provide a seamless guest experience throughout the hotel’s entire property, front and back end.
This, of course, takes a lot of work as more and more channels are added, but it can be a very fruitful exercise for any hotel as, at the end of the day, they’re able to provide guests with a fantastic guest journey. That fantastic guest journey is a big driver for us in the Payments Industry, too– we are trying to inspire hotels to understand where payments can help them in their business.
 |
Threat Actors
There are multiple agents who are the “bad guys” threatening a hotel’s security. The first one of them is cyber gangs, and among other tactics, they may try to steal cardholders’ data or use ransomware attacks – software that “kidnaps” a business’ systems and demands a ransom payment in order to stop the disruption or in exchange for not exfiltrating data.
Secondly, there are state-sponsored attacks. Hotels have information on certain persons of interest and their location, as well as that of their associates or other important people they are meeting with, which can be useful knowledge for governments.
Lastly, we cannot forget about competitors, who may be interested in information about the rates of other chains in order to benefit their own operations, and due care must be taken to protect that type of data, too.
With that in mind, I’ve developed this checklist of steps to consider when developing the cybersecurity action plan for your hotel, to ensure that you are adequately managing the risks to your customers, your property, and your reputation.
The Hotel Cybersecurity Checklist
1. Assign Cybersecurity and Privacy Specialist roles
Hotels need to staff these roles even though the technology isn’t their core business. These will be the people guiding the efforts of the rest of the personnel, as security is everyone’s job.
2. Identify and assess risks for all sensitive data
 |
Conduct audits of all data handled by your hotel that can be considered sensitive in order to understand your risk profile, including the systems used to process and store data, and then map the data flow to identify all the places where information can be.
Common points are legacy systems, which are hard to protect against new threats and to connect to new solutions in a secure manner; inexperienced or temporary staff who may not follow security protocols thus becoming a bridge by knowingly or unknowingly deploying viruses to the network; bad habits, such as staff writing credit card numbers in pieces of paper when in a rush or keeping passwords in unprotected places; and third-party systems with which hotels exchange information such as payments, reservations, invoicing, door locks, TV access, and many other types of vendors that are necessary for daily operations.
Once this is done, list down the threats and risks that may affect the data, considering the possible threat actors and attack methods your system may be vulnerable to.
3. Protect the data and key systems
 |
When all the data, systems, and possible threats are identified, it is time to protect them – especially your crown jewels. Knowing what needs to be protected ensures that you will be able to choose a security solution to apply, as well as an ideal secure configuration to harden all of your key systems.
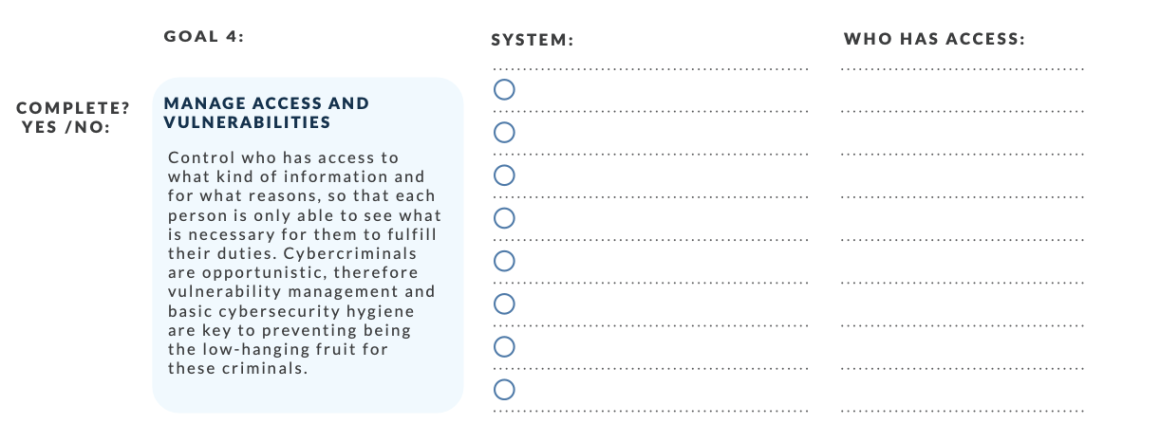
4. Manage access and vulnerabilities
Make sure you grant appropriate levels of access to each department or role in the proper way, by managing access privileges and monitoring them. Control who has access to what kind of information and for what reasons, so that each person is only able to see what is necessary for them to fulfill their duties.
Often, cybercriminals do not target specific businesses, they are just opportunistic, and thus make use of bots to find vulnerabilities that can be exploited. Vulnerability management and basic cybersecurity hygiene are key to preventing being the low-hanging fruit for these criminals.
5. Monitoring
 |
Monitoring access regularly helps in identifying breaches or leaks early, and gives you time to react to them. Keep track of traffic of users, applications, and networks.
6. Deploy malware protection
 |
Many companies think that simply having an antivirus solution means they are safe, but malware is very dangerous. It’s necessary to pick the best solution, configure it properly, and make sure that it’s deployed everywhere, and that it is indeed effective.
7. Deploy endpoint protection
 |
Endpoints (such as mobile devices, browsers, and office computers) are usually the first step in the biggest cyber attacks, as criminals rarely start attacks with something big, like going directly for servers. They’d rather attack one person to get access to that person’s workstation and then use it as an access point to go deeper into the company. Monitoring network traffic at each endpoint is crucial, and if you detect attacks at a very early stage, while still at the endpoint, you may be able to stop most of the attacks.
8. Manage legacy and third-party systems

Your systems may interact with that of third-party vendors or suppliers, so it is necessary to manage that interaction and ensure its security. There have often been incidents in the last years, usually very large-scale ones, where the culprits were hacked vendor systems which then allowed access to other businesses’ data. As for legacy systems, they tend to be more vulnerable as security patches stop being released, making them susceptible to modern forms of attack.
9. Build awareness and prepare for the worst
 |
Provide good training to employees on how to spot phishing and other sorts of attacks conducted by cybercriminals to decrease the likelihood of one of them becoming the access point. However, it is important to introduce and periodically improve incident management processes: have procedures in place in the case of an emergency or a disaster caused by a successful attack, meaning keeping constant backups and setting recovery processes in place.
10. Test your security
 |
Last but not least, test your security often. Conduct penetration testing to verify your security level and make sure it is up to par. This can be done through auditing, conducting technical tests, or using external or internal penetration testers to verify the actual security of your systems.
Download the full checklist >
Tags:
Aleksander Ludynia
Chief Security Officer
Feature
Hot Solutions
Hotel Software
Hotel Solution
Hotel's Cybersecurity
Shiji Group